
Safeguard Your Business Through Our Professional Cybersecurity Solutions
iSecurity by Flowz is your Managed Security Service Provider (MSSP) defending your digital landscape with cutting-edge cyberdefense solutions.
iSecurify is Critical for Cyberdefense
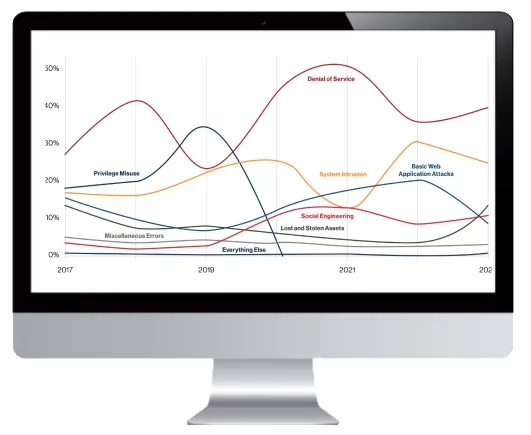
iSecurify helps companies deal with more risks as they grow. When businesses get bigger, enter new industries or places, and handle more sensitive data, security becomes more important and harder to manage. Threats keep increasing every day in different ways, but iSecurify can help solve these problems.
Benefits of Working with iSecurify
iSecurify gives organizations a big advantage with top-notch security advice, setup, and handling. Our teams are made up of many experts with decades of real-world experience in cybersecurity across different industries. We offer unique advice that boosts defenses, lowers the chances of problems, and helps recover quickly if something goes wrong.
What to Look for in an MSSP
When choosing a cyber security partner, check how much they know and how wide their skills are. Also, see if they can adjust to your needs. The really good ones are dedicated to helping you upgrade your organization’s security by being ready ahead of time and offering customized help.
iSecurify’s core values are all aimed at those ends:

Serve above all else
We subordinate our individual interests to advance others and provide value before expecting anything in return.

The right way is the only way
We always act with integrity in every situation so people can move forward.

Commit to what you say
We follow through and deliver our assurances by going above and beyond, never anything less.

Serve above all else
We facilitate the growth of ourselves and the elevation of clients with the art of Shoshin.

Serve above all else
We remain deliberate and focused on the work of the mission to give people the freedom to operate and grow.
Streamlined Compliance Management
- Assessments and certification for Industry-based regulations like HIPAA or CMMC
- Long-term maintenance of location-based regulations like the CCPA or EU GDPR
- Auditing and reporting for operations-based regulations like PCI DSS or SOC 2
- 61% Greater security competence
- 52% Improved quality of protection
- 43% Improved accuracy of decisions
- 36% Improved regulatory compliance
- 28% Reduced cost / overhead
- 61% Greater security competence
- 52% Improved quality of protection
- 43% Improved accuracy of decisions
- 36% Improved regulatory compliance
- 28% Reduced cost / overhead
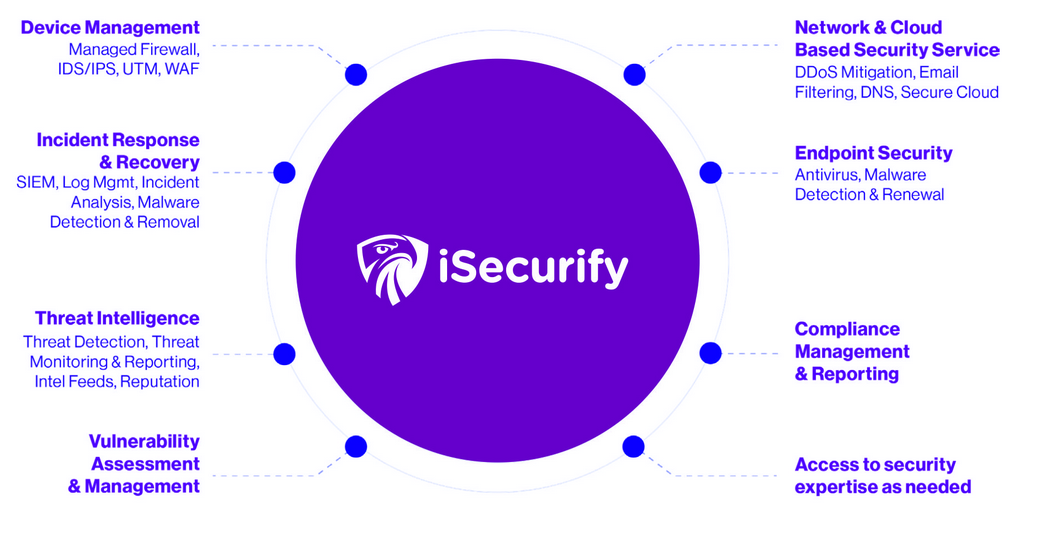
Solutions we provide
Virtual Chief Information Security Officer Services
- Security Operations
- Security Architecture
- Access Management
- Cyber-risk Analysis
- Loss Prevention
- Governance And Compliance
Security Testing Service
One of the most critical aspects of a sound cyberdefense strategy is regular security testing. A testing program ensures that your organization understands what data is under its control, how it needs to be protected, what it needs to be protected from, and the extent to which protections installed are functioning as expected.
- Hardware Pen Testing
- Mobile Pen Testing
- Network Pen Testing
- Web App Pen Testing
- Cloud Pen Testing
- Firewall Pen Testing
iSecurify has partnered with countless organizations to develop pen testing and general security testing services to meet and exceed their security needs. Our experts will first assess your defense systems and the data security requirements applicable to protected information classes, then devise multiple rounds of testing to identify, analyze, and eliminate any weaknesses in your architecture.
Phishing & Social Engineering Attacks
Phishing is a kind of social engineering attack. Criminals send messages that look legitimate, trying to trick you into giving up sensitive data or downloading malicious software. Some phishing attacks get caught in firewalls and filters built into your IT environment. Make sure those are installed and always be on your toes to catch any that slip through the cracks.
- What is Phishing?
- How Common is it?
- Can You Prevent It?
- Tell-tale Signs
- Plenty of Phish!
- Protect Yourself





























